Trusted Camera - Offline Version
The diagram shows an "offline" version of the camera - no external connection is required. This
would be the case in many applications - journalism, data gathering, scene-of-crime photography etc.
The manufacturer maintains a secure facility where pairs of public and private keys are generated.
The public keys are stored in a safe place and also published on the Web. The private keys are
embedded in the camera hardware, ideally in a microchip such as a field-programmable gate array or
programmable device with copy protection, so that it is not trivial to read the key back.
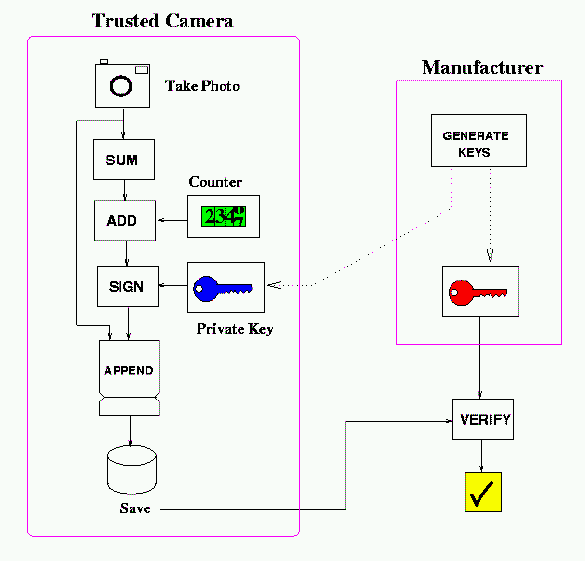
Operation is as follows:
- A digital image is taken using a CCD or similar device.
- An MD5 checksum is made of the image object.
- The output of a tamper-proof counter is appended to the checksum. The counter may incorporate
a free-running
clock (that is not settable by any method, such as user controls or battery removal).
- Optional metadata, such as a user-generated title, frame number, or GPS location, may be also appended.
- The checksum and metadata are digitally signed with the camera's private key.
- The signed checksum and metadata are appended to the image object.
- The image is saved to memory.
To verify the authenticity of the image, the public key may be retrieved from the manufacturer's
website using the serial number of the camera. Public keys themselves may be digitally signed by the
manufacturer as a guarantee against tampering on the public website.
The signature on the image object may then be verified using the public key.
Since any cropping or scaling of the image will invalidate the signature, it may be useful
if the camera encodes and signs several resolutions simultaneously, for instance a full-size image
plus a thumbnail.
For still images, operation is relatively simple. A signed checksum exists for each image, and
may be identified by, for instance, filename (img001.jpg, img.001.sig, img002.jpg, img.002.sig....).
The signature object may also include a reference to the image by name or frame number.
For video, the issue is more complex. Each frame, or selected frames, may have a checksum, several of
which may be combined under one signature. For a video sequence stored as e.g. an MPEG file, there
is then a corresponding signature file which refers back to frame numbers within the MPEG data.
Possible Uses
Limitations
- A sufficiently determined attacker with physical access to the camera may extract the private key.
It may then be possible to clone the key and generate falsified images with altered counter settings,
and possibly to restore the camera to normal operation. However, the counter would indicate any
duplicate images. It might be simpler to steal the camera, take photographs, then restore it.
In military and espionage applications, chips have been fitted with explosive or acid layers to
deter physical examination.
-
While the private key and signing mechanism may be integrated into one device with the
camera operating system, the imaging device, usually a CCD, would probably be separate.
It may be possible to inject a fraudulent or time-delayed image into the camera instead of
the signal from the CCD.
-
The image may be trivially falsified by pointing the camera at a printed photograph or
television camera.
Back to Main Page
